Published
Last 1 week
Last 30 days
Latest 24 hours
Seniority
Published
Profession
Industry
Seniority
1
jobs
HR-EX Consulting
Lagos, Nigeria
Eat 'N' Go Limited
CLOSEDLagos, Nigeria
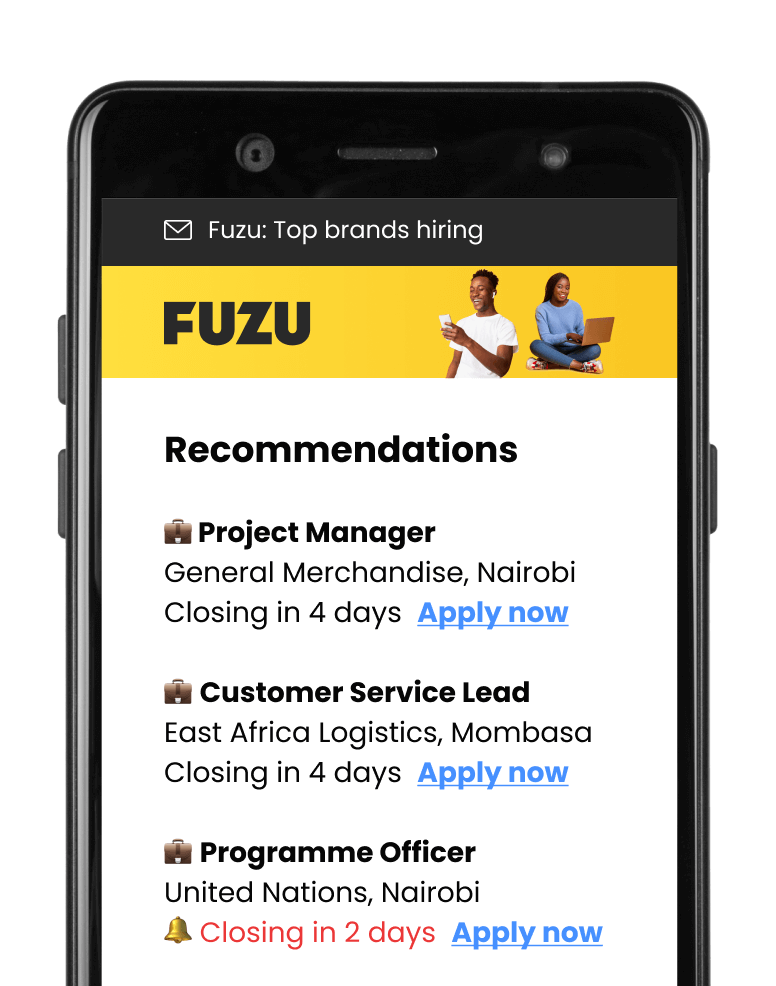
Get personalised job alerts directly to your inbox!
Food Concepts Plc
CLOSEDLagos, Nigeria
Closing: May 23, 2024
8 days remainingPublished: May 8, 2024 (8 days ago)
Education:
Work experience:
Language skills:
Contract Type:
Sign up to view job details.
Education, Experience & Skills Required
Education, Experience & Skills Required

Applications submitted via Fuzu have 32% higher chance of getting shortlisted.